How to protect your Small / Medium business from cyber-attack
97% of New Zealand Business is categorised as SMB, but how at risk are SMBs really? Whilst the headlines are usually filled by hacks involving large companies, don’t be fooled into thinking that cybercriminals discriminate by size. Actually, some of the biggest data breaches start out at smaller businesses. SMBs perform services to enterprise level companies and have some form of access to their systems e.g., an HVAC contractor delivering services to a large retail chain was hacked and their access used to breach the retailer.
So, why are SMBs a target?
Your valuable data – hackers know that even SMB data is easy to profit off on the Dark Web – do you hold medical records, credit card details, bank account details or perhaps proprietary information? The crims either use it themselves to get into bank accounts and commit fraud or they sell it to other criminals.
Your links to larger companies – we live in a world where businesses are digitally connected to each other for a variety of reasons – manage supply chains, share information, complete transactions etc. Enterprise organisations are usually harder to breach, making the smaller business partner a viable target to get into the systems of the enterprise client.
Your hard-earned dollars – Cybercriminals mostly target companies for profit, particularly in New Zealand. With the primary motive to make money, it is easy to see why ransomware is such a popular method of attack. As long as they are getting away with it, it will continue.
How do you protect your business?
You may wonder how you can protect your business sufficiently when unlike enterprise companies, you cannot have an entire teams devoted to managing cybersecurity.
For SMBs, we recommend the guidance as detailed in the ACSC Essential Eight Maturity framework. The framework is simple and guides you through four maturity levels – each step up caters to protection against a more sophisticated attacker.
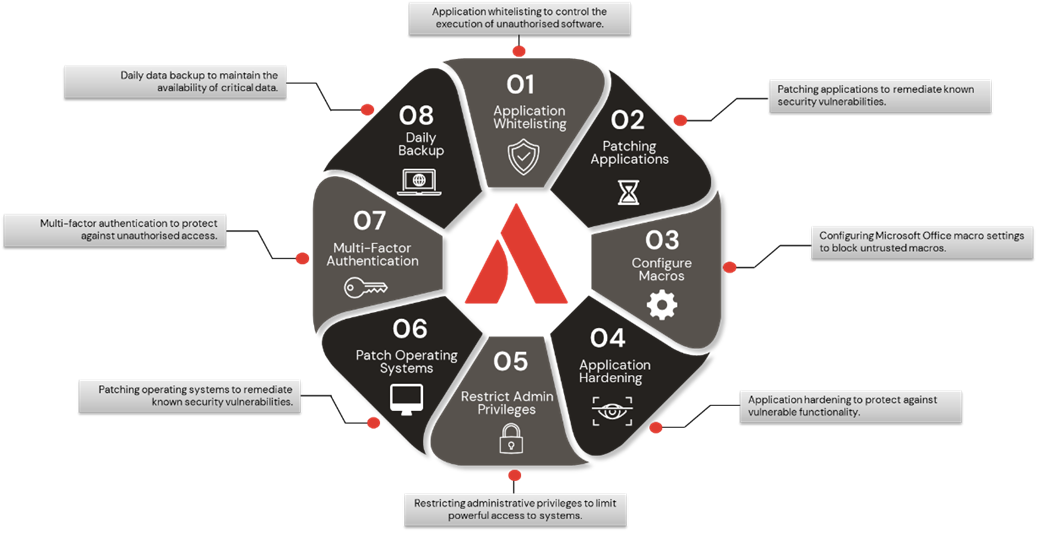
How you can implement Essential Eight in 5 steps
ACSC Essential Eight is summarised in the diagram below. As discussed, there are four maturity levels (level 0 – level 3) within each control – focussing on these controls and building your maturity to a level that fits your risk profile will go a long way to safeguard your business from cyber-risk.
Step 1: Review the key elements of the model
Step 2: Identify a target maturity (this is not what you think is realistic to achieve, but rather the risk associated with exposure to more sophisticated attacks given the nature of your systems and data requirements)
Step 3: Recognise that the Essential Eight represents a minimum set of preventative measures – you may need to consider further strategies
Step 4: Plan to implement
Step 5: Build a Team – IT Security is not a set and forget things and responsibility should never lie with a single person. The skills shortage, complexity and cost attributable to building a team, partnering with a MSSP often represents the most viable solution to a SMB. In this way, you are assured that someone is 1) tracking key changes in the threat landscape 2) you have a vendor and product suite that is fit for purpose, provides relevant service metrics 3) alerts are managed and acted on 4) AI and human resources are applied to provide timely prevention, mitigation, and response activities.
Cybersecurity is a journey, not a destination. By improving your cyber-security maturity, you are raising the cost of attacking your business i.e., if you present a harder target than your neighbour, adversaries will generally redirect their attention.
For a discussion on how you can improve your security posture and to learn about the unique Advantage approach to managing cyber-security risk for SMBs, give us a call on 0800 358 8999 or send us a message here