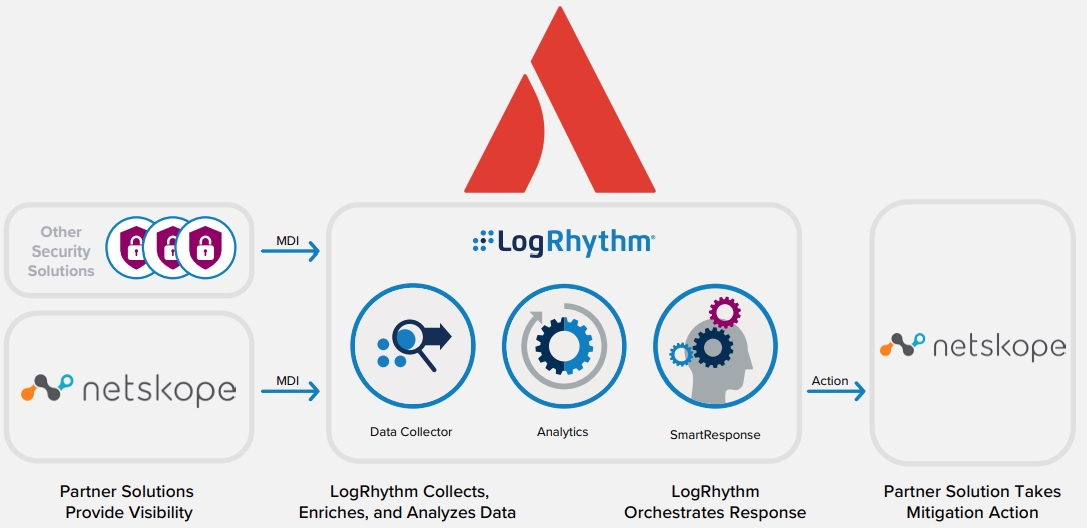
As logs are ingested into the LogRhythm NextGen SIEM Platform, the Netskope SRP uses the Netskope RESTful API to add suspicious URLs, files, and SHA-256 hashes to Netskope’s blacklist. This can be performed from custom AI Engine rule sets or manually from the Web Console. The SRP also stores a local copy in the LogRhythm List Manager. If a threat feed indicates questionable browsing habits in LogRhythm, a security analyst can use the Netskope SRP to add the suspicious URL or file to the LogRhythm List and Netskope’s blacklist.
[pdf-embedder url=”https://advantage.nz/wp-content/uploads/2022/05/Netskope-JSB.pdf” title=”LogRhythm Automates Blacklisting of Suspicious URLs and Files”]