Spoofing a company’s credentials, their domain and brand is becoming a common way that cybercriminals use, sending an email that looks as if it is coming from you. They may impersonate people who are known to and trusted by the recipient, giving a layman the confidence to respond to requests for information they would typically not reply to. It can be highly successful and hugely costly.Vendor Email Compromise (VEC) attacks jeopardise company brands in what is probably our most common means of communication today. Wouldn’t it be great if those emails didn’t even make it to your server?
DMARC is an email authentication protocol that acts as an instruction manual for a receiving email server. Every time an email gets sent from your domain, the receiver’s email server checks your DMARC records (published on your DMS) and validates the email.
If the email is legitimate, it ‘passes’ DMARC authentication, and gets delivered to the user’s inbox.
If the email is from an unauthorised sender, depending on your DMARC policy, the email can be either sent directly to spam, or even blocked outright.
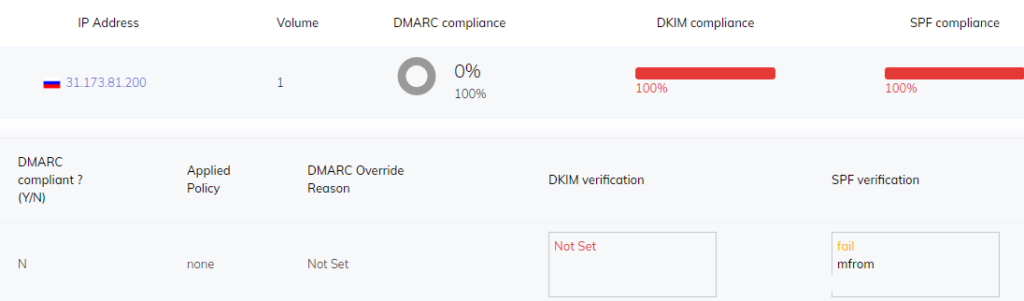
Advantage offers you PowerDMARC which provides you with:
• Around the clock visibility of your email data flow
• Prevents your domain from being spoofed and used to launch email phishing attacks
• Access to comprehensive IP threat intelligence feeds supplied by our renowned technology partners
• Protection of your public-facing domain and improves your brand reputation.
• Get real-time alerts when a spoofing attack is detected on any of your domains
Find more information about the risks of email phishing and the damage it can do to your brand here.
