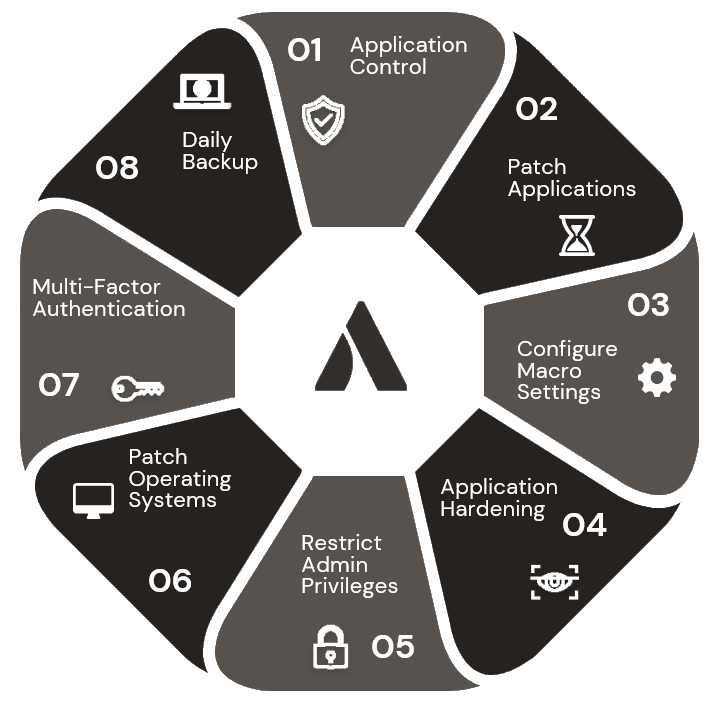
A product of the Australian Cyber Security Centre, The Essential 8 (or E8) is a set of controls which, when used in combination, make your organisation much harder to hack than, well, anyone who isn’t applying them. And here’s the thing: a ridiculous number of businesses aren’t applying them, making them a more viable target than your own good self.
And that’s a pretty important distinction. Those of us working in cybersecurity will tell you, ‘it isn’t a matter of if, but when’. Cybersecurity is difficult. It’s harder than hacking because good cybersecurity must identify and mitigate ‘every’ potential hack, while the attacker needs only specialise in one. The hacker, too, doesn’t necessarily care who his target is; he’ll have a go at anyone, moving past the ones which give him a headache, and on to the lower hanging fruit.
You don’t want to be that fruit. And with E8, you won’t be. It’s like that old saying, you don’t have to outrun the lion, you only need outrun your companions.
With that in mind, let’s get stuck into E8. The controls (and a few added insights) are:
- Application control. Quick wins here include blocking targeted application types using group policy. We advise implementing Microsoft’s block rules (including driver block rules), and restricting Admin privileges so users can’t install random applications. Simple interventions which can save a lot of grief.
- Patch Applications. Again, and again and yes, yet again we see hackers getting through thanks to deficient patch regimes. Yes, there’s a lot of software out there, yes, it’s a hassle and disruptive, and also yes, it is crucial. A thorough, mature patch regime is worth its weight in gold; gold which would otherwise go to a hacker. Quick wins? We’ve got them. Implement your patch regime in conjunction with control 6, Patch Operating Systems and kill two birds with one stone. Set applications for auto update where possible…and don’t forget the Antivirus products need patching, too.
- Configure Macro Settings. Aah, macros – keeping security people busy since forever. Disabling macros altogether is the best option but isn’t always possible. For quick wins on macros, you’ll want to limit, restrict, and manage macros including subjecting them to AV scanning, and only running in sandboxes, from trusted locations, or digitally signed publishers.
- Application Hardening. That’s the fancy name for making sure your applications are buttoned down to do only the things you want them to do. Most applications have a degree of flexibility and versatility which means they have functions you don’t use or need. In the old days, most applications were left ‘open’, leaving back doors for hackers. The good news is that quick wins are easily achieved and include using Microsoft’s Attack Surface Reduction tools/rules, enabling logging, and monitoring on all apps, and removing unsupported software. There’s a lot more to application hardening, so a thorough examination of all software is usually the first place to start for comprehensive application hardening.
- Restrict Admin Privileges. Here’s the thing. Very few of your people should need or have admin privileges…but how many of them are thus enabled? Probably too many. 95% of users do not need local admin rights…so they should not have them. Cleaning this up might take some legwork, but once done it’s a lasting benefit.
- Patch Operating Systems. Look back at #2 on this list; patching OS is just as important as patching applications, and these tasks should be done in conjunction. It’s a good idea to stay on top of Microsoft’s lifecycle policies – and this is not a mystery, but something Microsoft (and any other OS vendors) telegraph well in advance.
- Enable Multifactor Authentication. You know why this is an absolute must. Combining authentication methods makes it an order of magnitude more difficult for an attacker. Select your MFA solution carefully and set MFA on all privileged (Admin) accounts.
- Daily Backup. Again, you know why regular backups are essential, there’s no need to spell it out. But remember: a backup is only as good as the restore, so test that aspect regularly.
While I’ve provided the high-level quick wins and ‘obvious’ methods of implementing the E8, there are differing levels of maturity which require a little more detailed attention. At the same time, at Advantage we use automation tools and technologies which accelerate the process of establishing the E8, while leaving nothing to chance. For example, we use Automox for patch management and configuration, so every endpoint is appropriately managed from a security standpoint. Got 1,000 devices? Patching them manually is a nightmare.
Then, for threat intelligence and understanding your threat environment, we use Tenable which combines visibility with business context to understand your cyber risk and prioritise mitigation. And we also use Armis for asset inventory, risk management, and detection & response.
So, that’s the Essential 8. These controls and recommendations are, as you’ll appreciate, common sense for security. Be that as it may, it’s worth stating again that all 8 are essential. Some combination of them will leave a gap, and any gap makes you a fruit ripe for picking.